|
Handy MultiChannel Proxy

Higher resolution
Handy Browser

Higher resolution
Handy Email

Click here for explanation
Handy File

Click here for explanation
Handy Messenger

Higher resolution
Handy Proxy
URL Dropping Feature


Click here for explanation
Handy Web Server
With Encrypted Page

Higher resolution
Handy Web Server
File Encryption

Higher resolution
Handy Look At HTTP/HTTPS

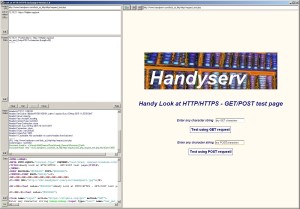
Higher resolution
| |
Handy Look At HTTP/HTTPS
(This program is part of the Handy MultiChannel Proxy package, to use it you must install the whole Handy MultiChannel Proxy package)
Handy Look At HTTP/HTTPS is a program designed for the Windows environment providing a way to explore the data exchanged between browsers and HTTP or HTTPS web sites
 |
Thanks to the program, you will be able :
- to have a look at the contents of HTTP or HTTPS pages
- to see the contents of HTTPS pages unencrypted - which demonstrates the uneffectiveness of the HTTPS data protection and that you need a better protection as the one provided
by the Handy MultiChannel Proxy
- to list all the links which are called when you visit an HTTP or HTTPS web page (including the hidden ones as .CSS or .JS)
- to visit one of these listed links (with GET or POST data) to obtain more details about them and what they do
- to explore handshakings between you and the visited web site including the exchanged data
- to edit the resulting data if you want to
|
 |
How this application works :
This program is made of two parts. The right side of its screen displays a Chrome-based browser with basic navigation features.
The left side displays the inner functioning of a "real browser" without any graphic interface in order to show all exchanged data.
Both sides are independent from one another. The Chrome-based browser allows the program to know all the visited links (including GET and POST data) in order to be used by the left part of the application.
When you click on a link listed on the left side of this program the Chrome-based browser doesn't do anything, only the "real browser" on the left side works.
|
 |
How to use the results :
When you have opened a page with the Chrome-based browser, you can click on a listed link and use all the resulting data with the Handy Browser (included in the Handy MultiChannel Proxy package).
There are 4 possible screens :
1 - the visited page or link "as received" including a warning about the fact that it was saved locally on disk probably causing the visible links to be non-operational
2 - the visited page or link "as received" without warning but with the same "limitation" as stated above
3 - the data received from the visited page or link in HTML, CSS or Javascript code
4 - the handshaking data exchanged between the "real browser" and the visited page or link
|
 |
Other example of use :
In the example below, we visited one of the well-known HTTPS web sites (layout is modified and web site name is hidden for obvious reasons). In this site, all links and exchanges are fully HTTPS/SSL encrypted,
however the encryption keys are PUBLIC. Therefore, everyone is able to develop a program like this one in order to catch exchanged data as Login and Password.
This is what we show in the example below where the Chrome-based browser was used to access the HTTPS site allowing the program to catch all opened links and exchanged data.
This means that your personal data are NOT SAFE when you access HTTPS web sites and that the SSL protocol can be easily bypassed.
Our goal in Handyserv is to make you conscious about these risks of having your data stolen and used by ill-intentioned people when you connect to the internet from a WiFi public access point, for example.
Then, we advise you to use our Handy MultiChannel Proxy that will overencrypt HTTPS exchanges between 2 interconnected Handy Proxies.
These proxies do NOT uncrypt HTTPS data and of course they do not modify them since they only overencrypt the data and send them to the other connected proxy which in turn will remove the overencryption
to retrieve the original HTTPS data.
Moreover, we invite you to discover our Handy Web Server With Encrypted Page that allows to create completely private web sites only accessible via the Handy Browser by duly authorized persons
(see our home page for more details).
|
|
Example of use with Posted Data

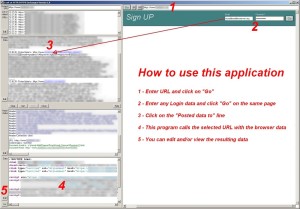
Higher resolution
In the example above you can see that the Login and the Password appear in clear on the left side although they were sent in HTTPS encryption mode.
This allows our program to use these informations to access the original web site as if it was the user himself.
|
 |
Important remarks :
Attention : this program must be considered as a debugger. It does NOT execute Javascripts, AJAX or
any other script which will make the visited pages non-operational (login to a web site will fail for example).
The main function of this program is to explore a visited link included in a web page in order to understand what it does and if it is necessary or not for the web page to be functional.
If its use is not obvious, you can drop it by using the URL dropping function provided by the Handy MultiChannel Proxy package.
Since the Handy MultiChannel Proxy is a "channel switcher" and a URL filter, when an HTTPS link is opened by a browser with the "CONNECT" function, the proxy lets the (encrypted) exchanged data flow as they are
(as explained above, the proxy can overencrypt the data flow if you wish so).
This means that once the channel is open (the CONNECT request succeeded) the proxy cannot filter any new link called inside the HTTPS data flow (.CSS or .JS links for example).
This implies that if you want to filter an HTTPS link you have to ask the proxy to filter the general HTTPS domain name or a specific HTTPS subpage/sublink.
|
Handy Browser, Handyproxybrowser, Handy Communication Channel, Handy Edit, Handy Email, Handy File, Handy Libraries, Handy Look at HTTP/HTTPS,
Handy Messaging Server, Handy Messenger, Handy MultiChannel Proxy, Handy MultiChannel HTTP/HTTPS Proxy, Handyproxy License Sharing, Handy Proxy, Handy Web Server,
Handy Webserver File Encryption are trademarks of Handyserv
|